Bonus - How to protect the Developer Environment
In the previous exercises we leveraged the Cloud One Platform to protect our applications and Application environment; but what about the Developers environment, the machines, and the Cloud Environment as a whole?
For that we will leverage two other Trend Micro Cloud One Technologies
Trend Micro Conformity
In this workshop, we learned how to scan our IaC templates with Cloud One Conformity, now let’s integrate our AWS account with Conformity to have a more holistic view of the possible drifts and misconfigurations within our 80+ different AWS services within a single multi-cloud dashboard. By integrating our AWS account with Cloud One Conformity we will be able to continuously analyze our risk status, remediate violations with step-by-step guides to improve our security and compliance posture.
For more information on Workload Security, please visit Trend Micro Cloud One™ – Conformity
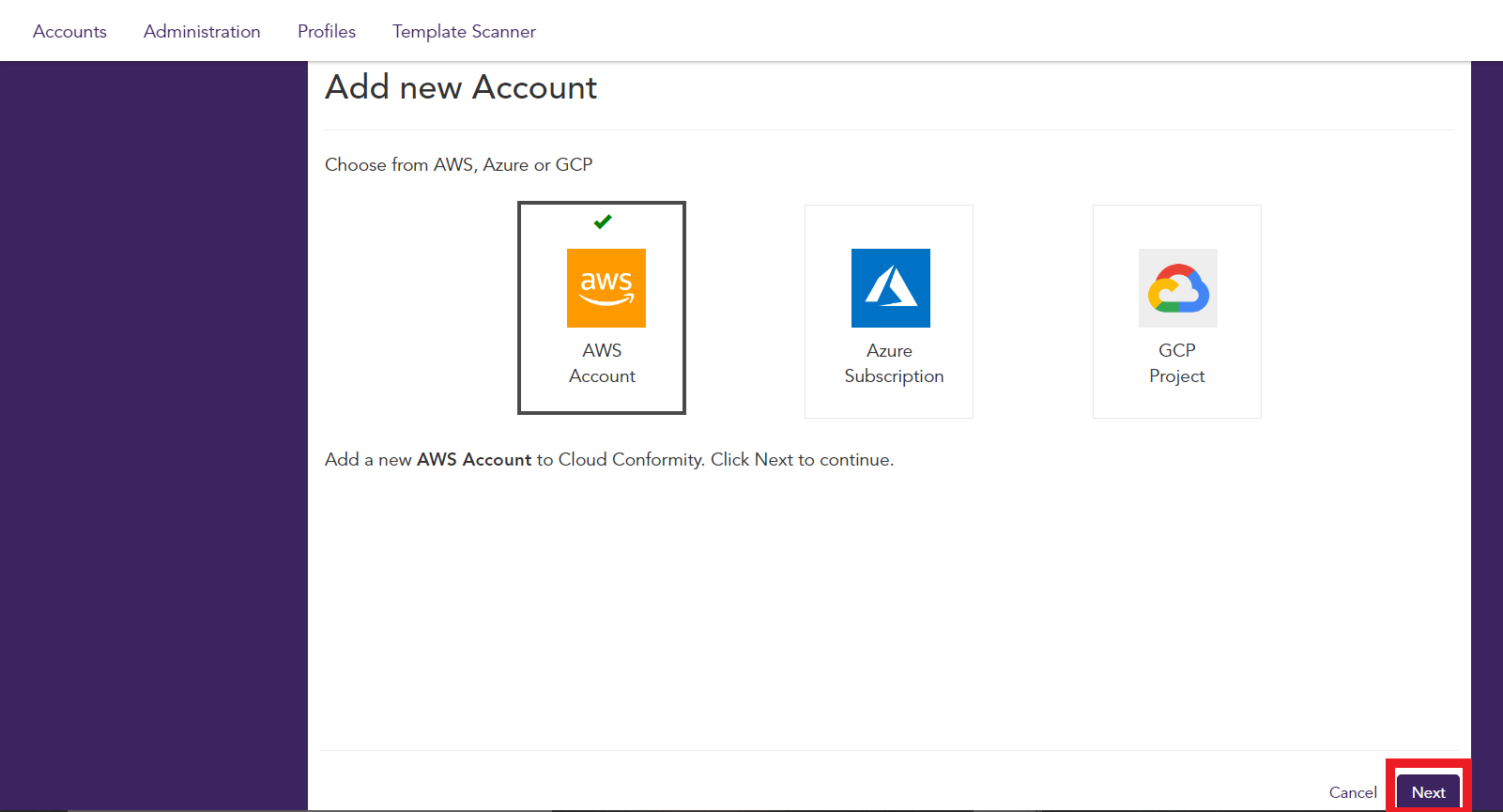
1. Log in to your Cloud One account and click on the Conformity box
1.1. Select AWS Account to add a AWS account
- Click Next
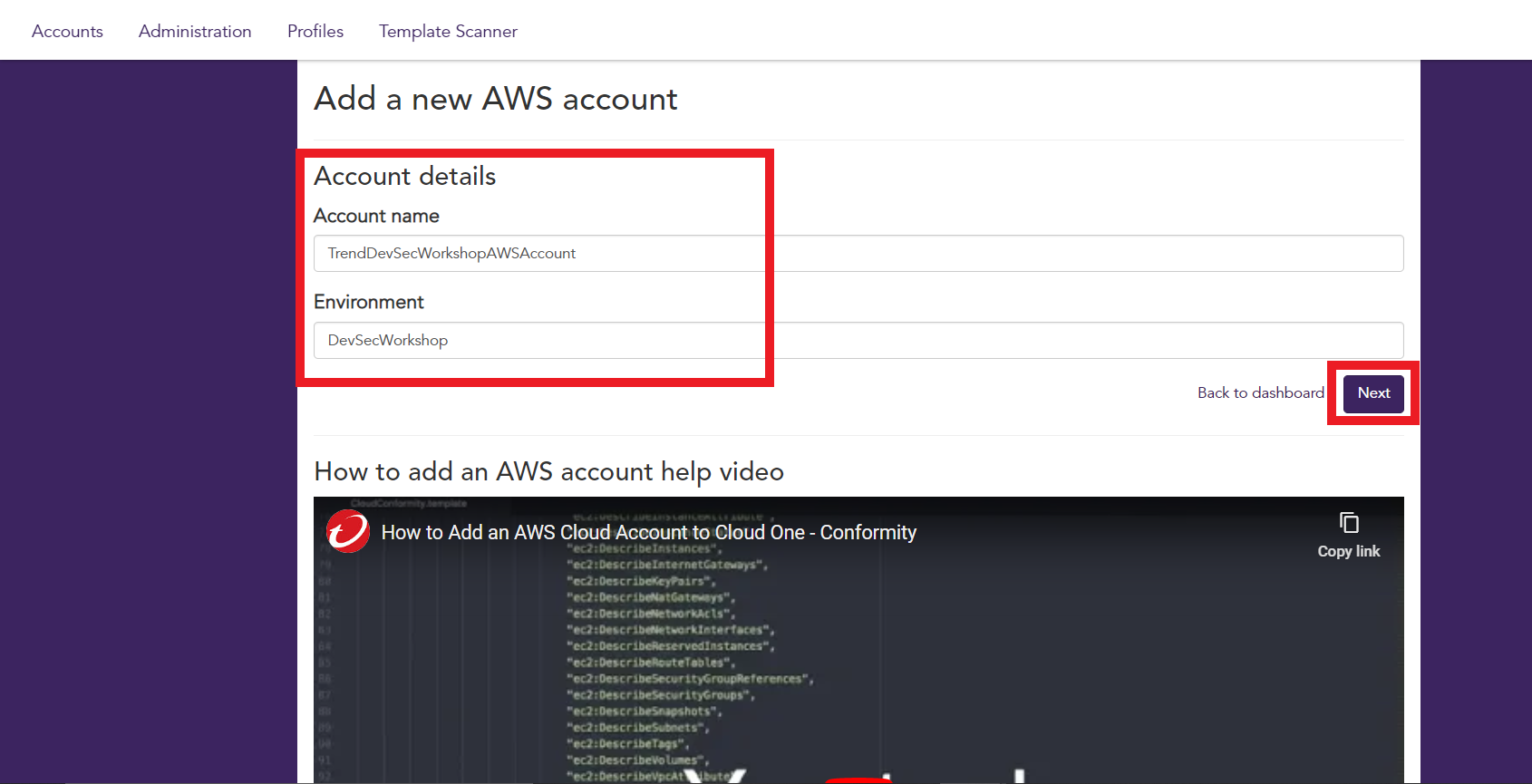
1.3. Give it an Account name and Environment name for the AWS account inside Conformity
-
Account name:
TrendDevSecWorkshopAWSAccount -
Environment Name:
DevSecWorkshop -
Click Next
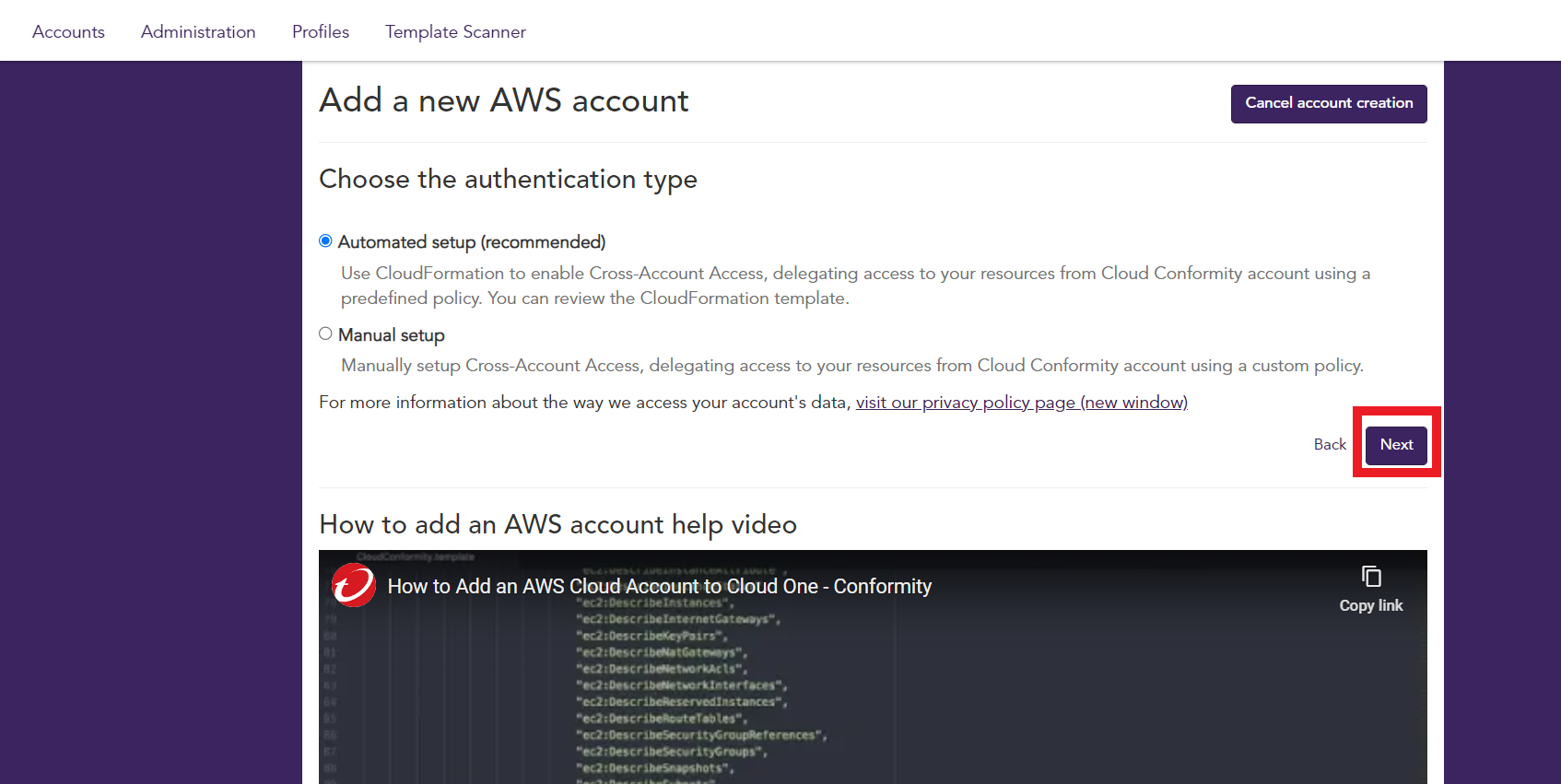
1.4. Select Automated Setup to use Cloud Formation Template and automatically integrate your AWS Account with Conformity
- Click Next
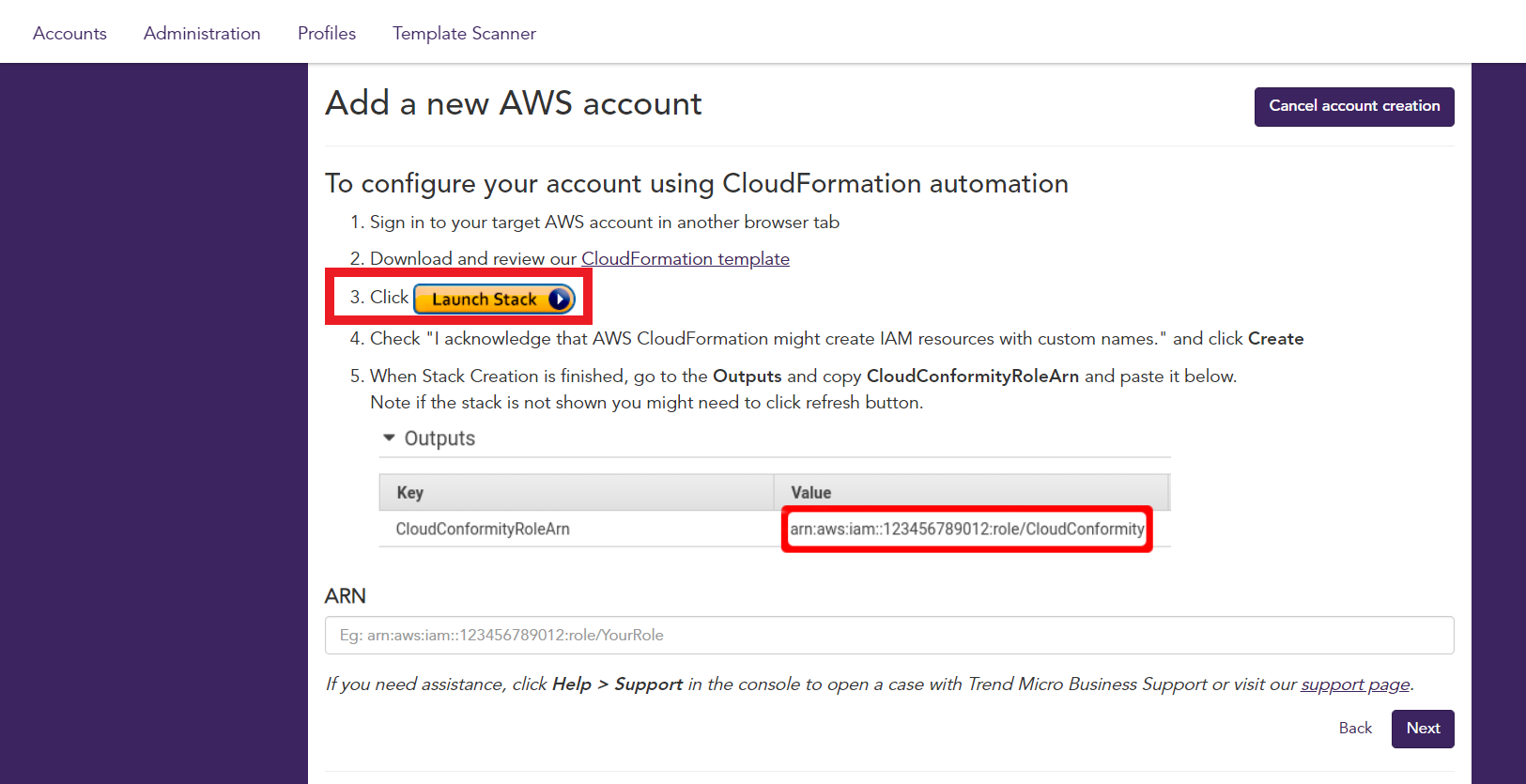
1.5. Lauch the CloudFormation Template in your AWS Account
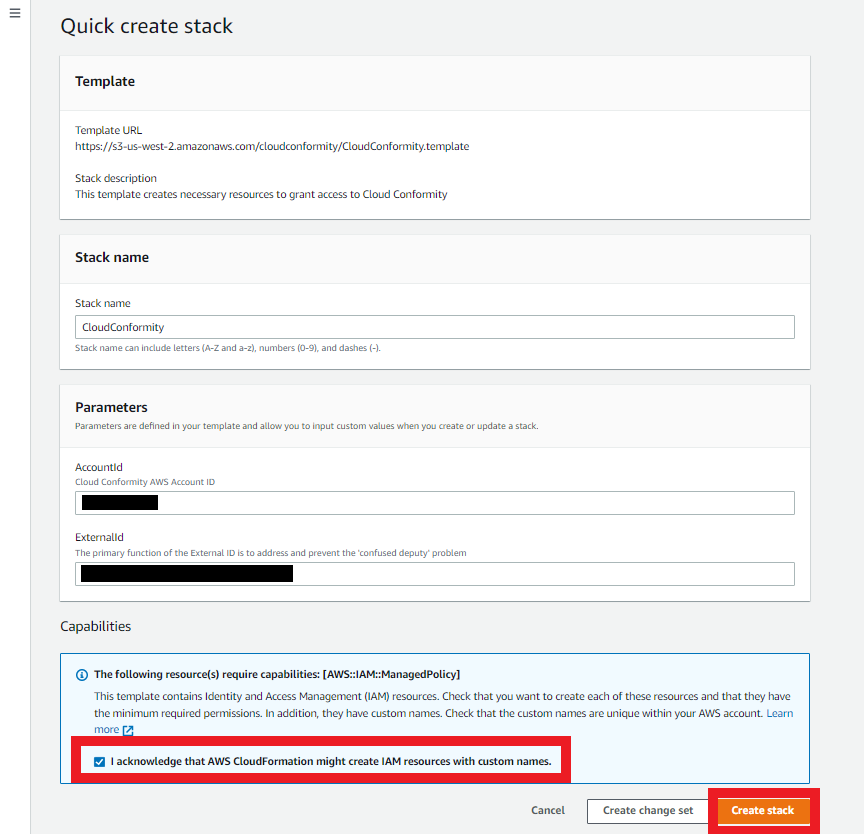
- In the same browser we are Logged on your AWS Account, click on the Launch Stack Button
- It will open a new tab, in your AWS Account
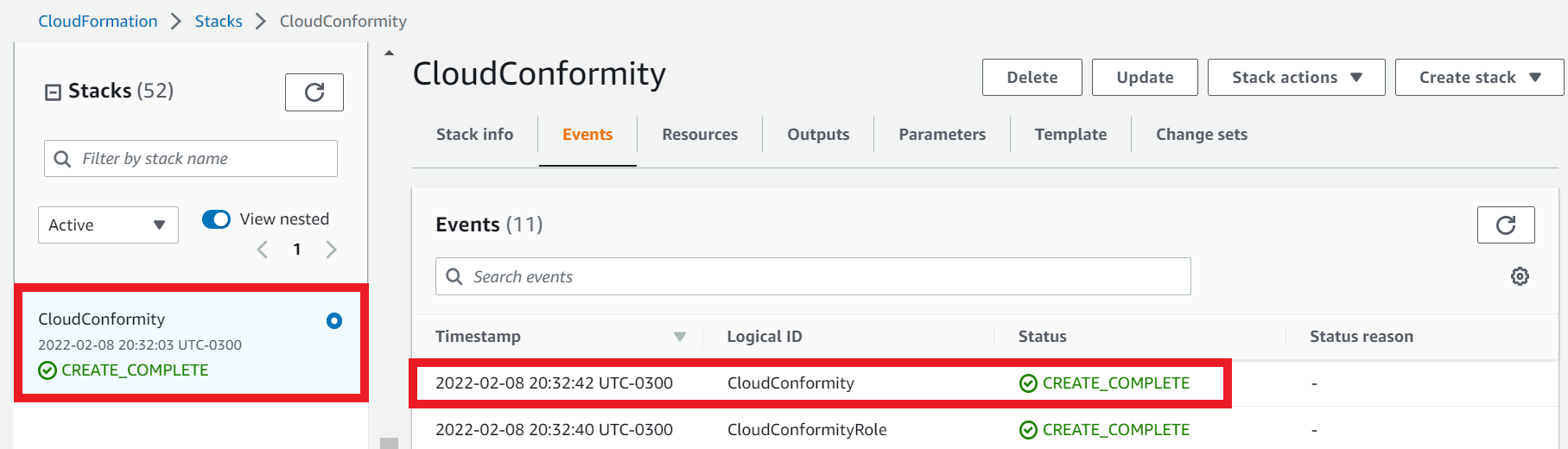
1.6. Ensure the stack status has reached Create_Complete
- Select the Stack info tab
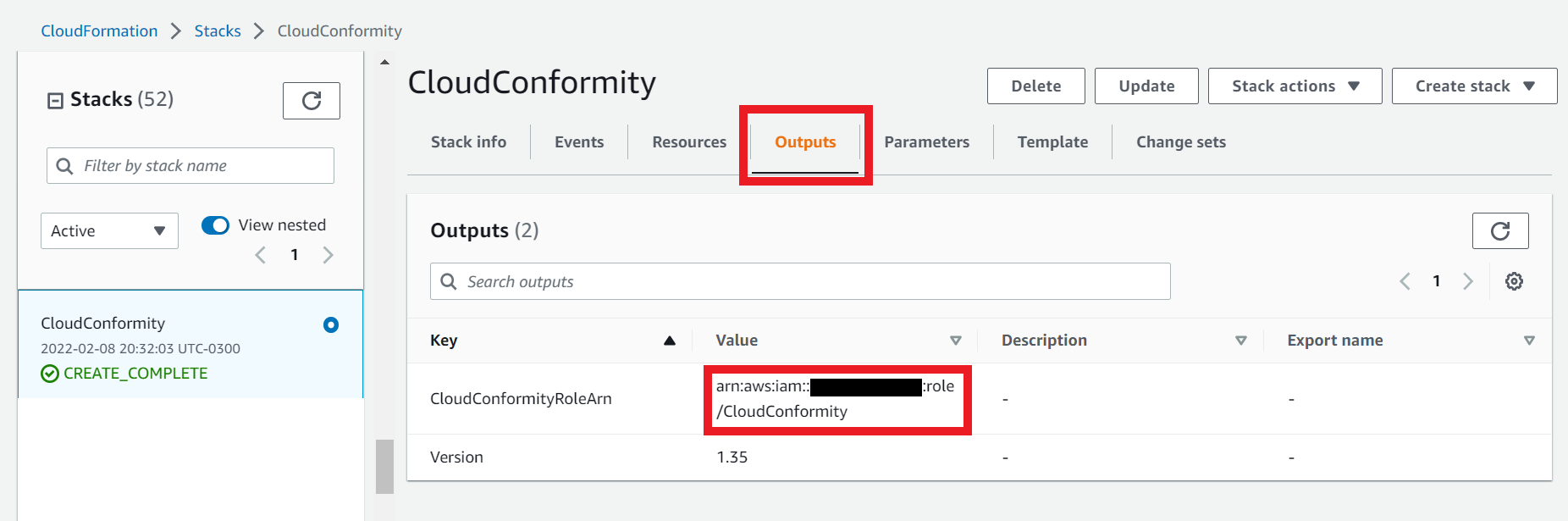
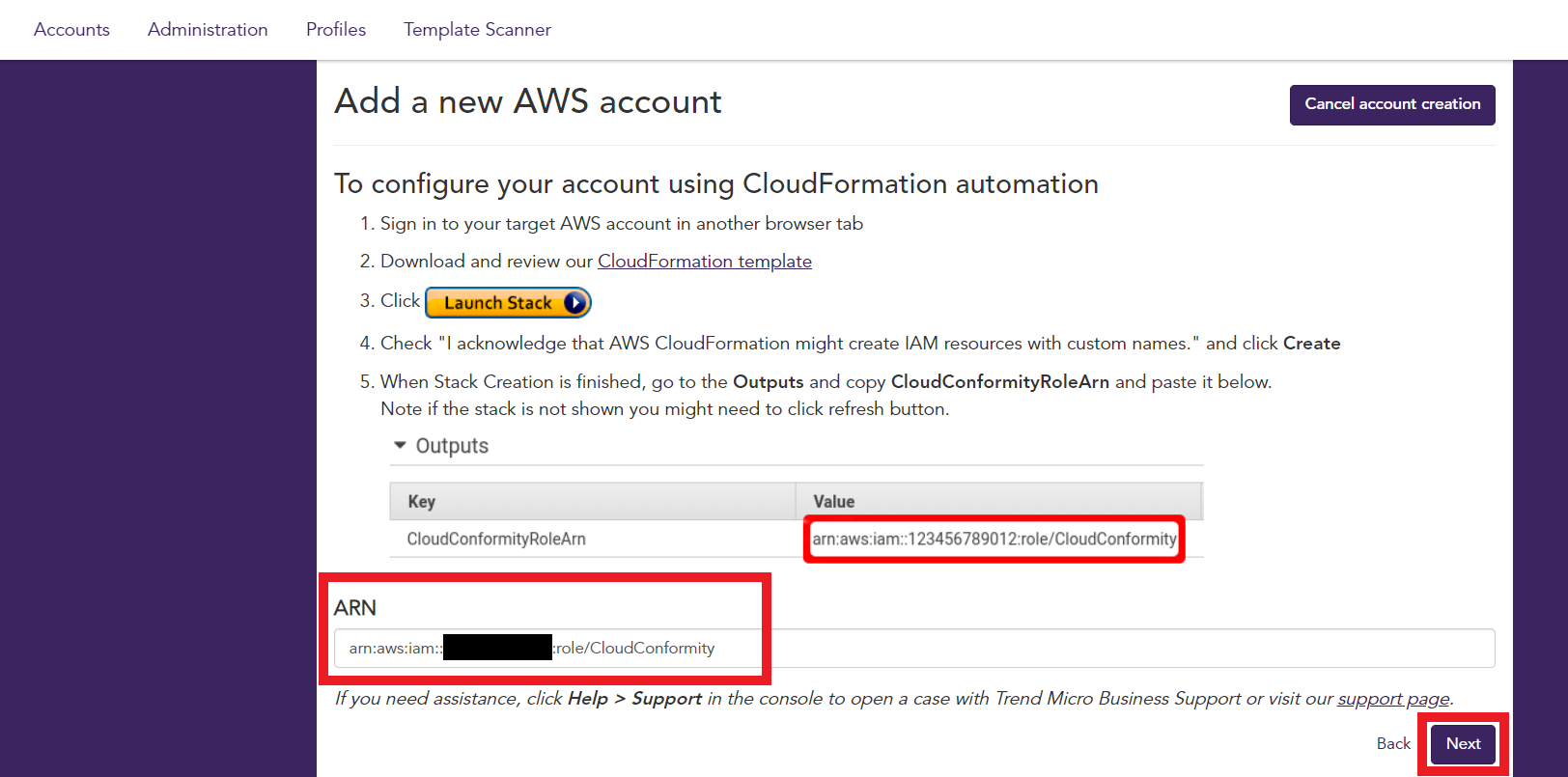
1.7. On the Outputs tab
- Copy the CloudConformityRoleArn Value
- And paste the value on the ARN field in Conformity
-
Then click Next
-
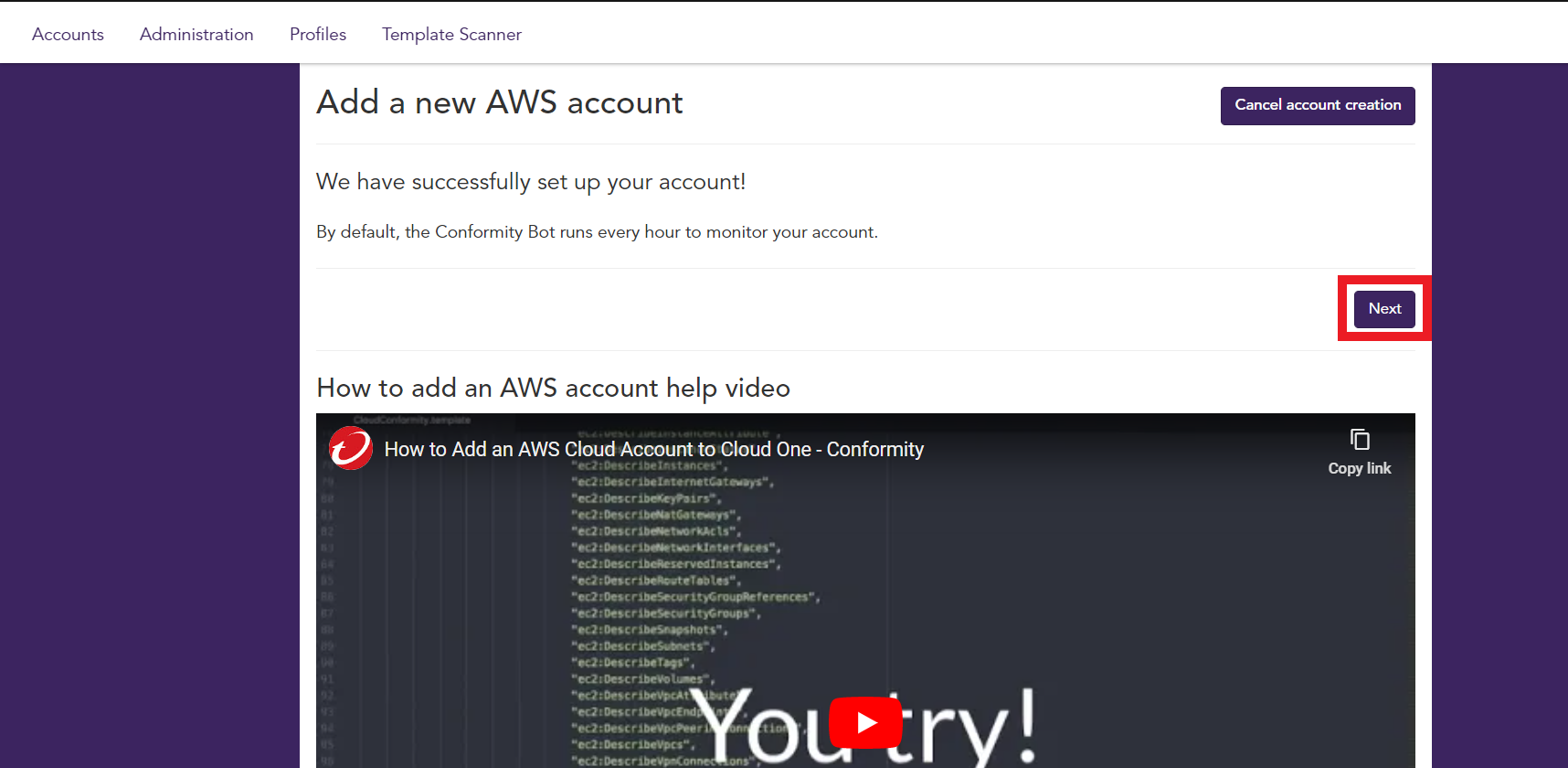
The Account was successfully set up
- Then click Next
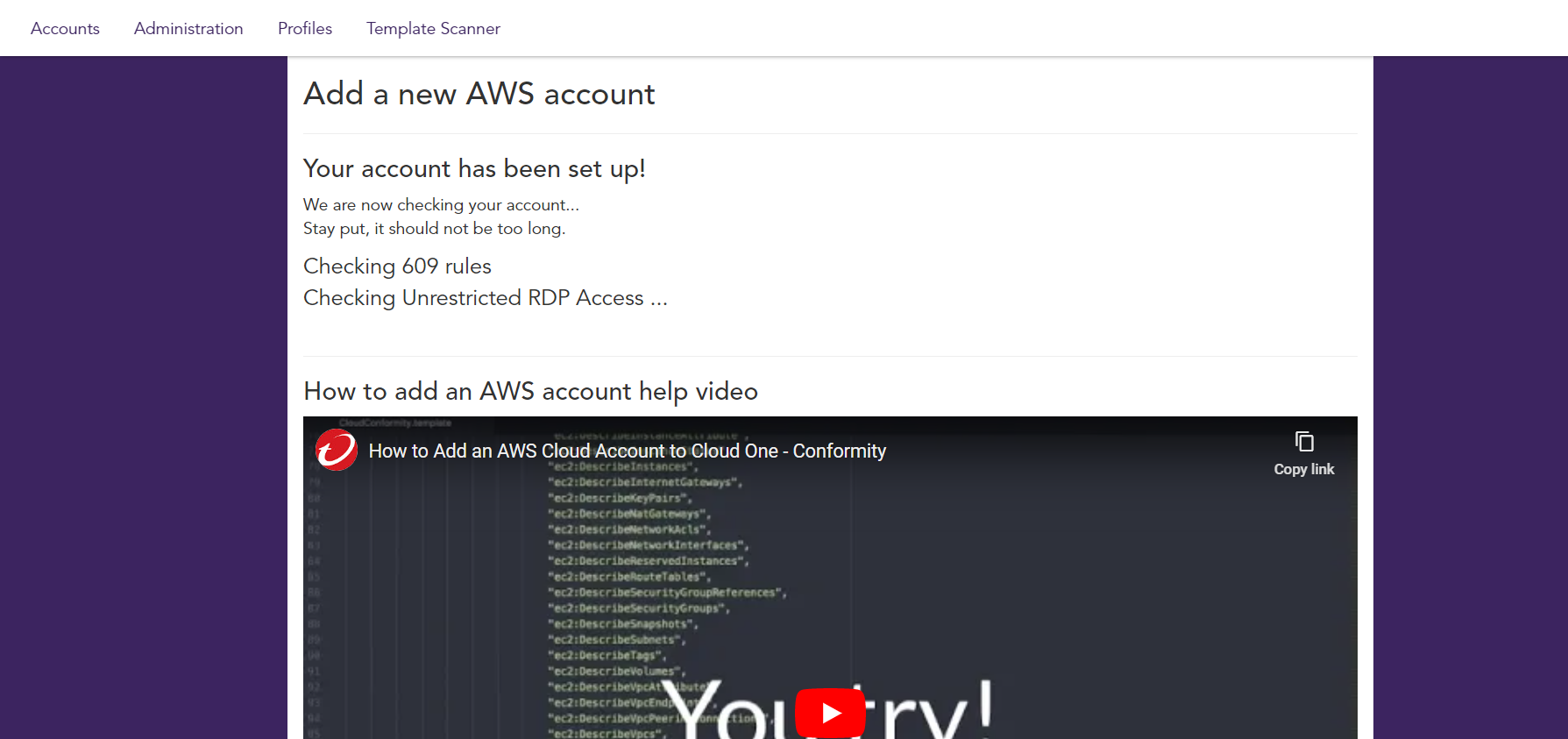
Wait until the first Scan is finished in the AWS Account
- Now in the Conformity Dashboard we could see areas that would require attention so that we could start applying best practices and remediations to improve our infrastructure.
If you want to explore more about Cloud One Conformity, we have a workshop about Securing AWS Infrastructure with Trend Micro - Cloud One Conformity - HERE -
Trend Micro Workload Security
Get started with Workload Security and embrace the robust server protection offered, so you can protect all your servers where you need it, without disrupting your business applications or processes.
For more information on Workload Security, please visit Trend Micro Cloud One™ – Workload Security
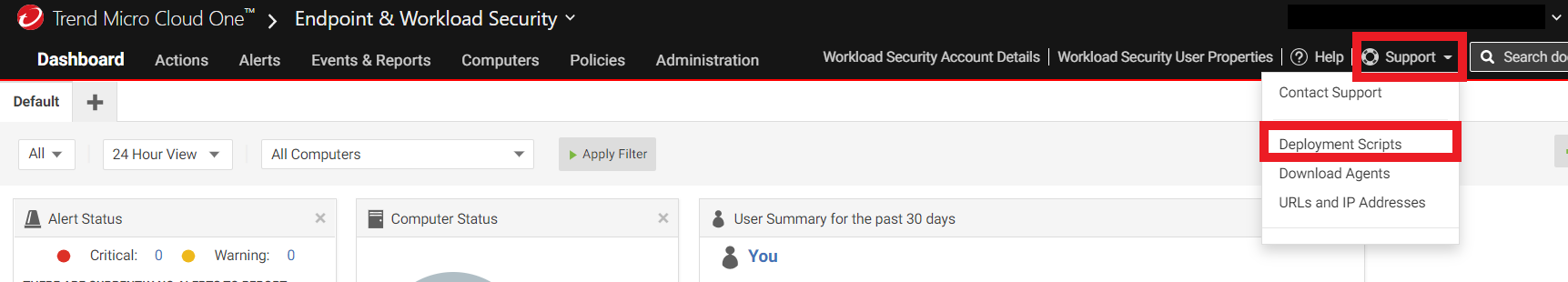
1. Log in to your Cloud One account and click on the Endpoint & Workload Security box
1.2. Click on the Suport button
- And Deployment Script
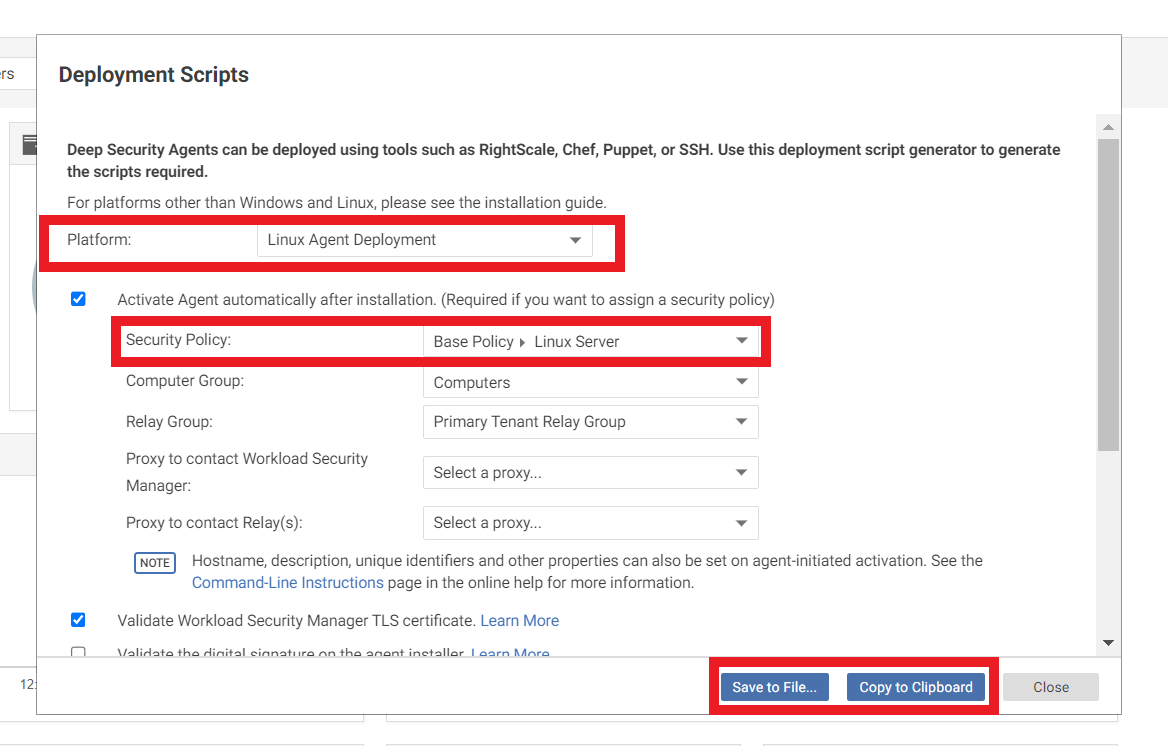
1.3. Chose the platform of your machine and a policy from the list
- Save to file or Copy to Clipboard the commands to download and install the agent in your machine
1.4. Let’s install the Workload Security agent on your Developer Machine
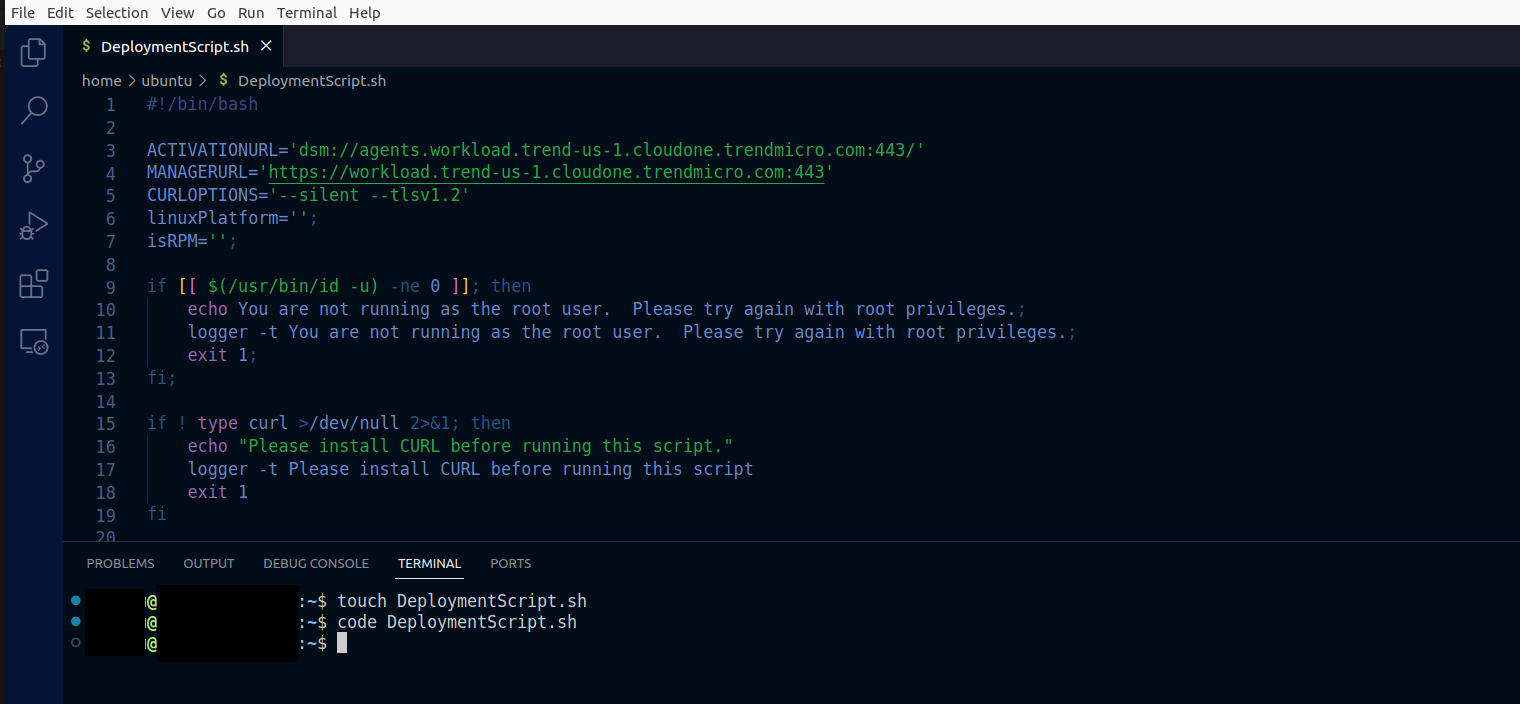
- In the terminal, create the file with the command
touch DeploymentScript.sh - Open the file
code DeploymentScript.sh - Paste the comands from the Workload Security Console
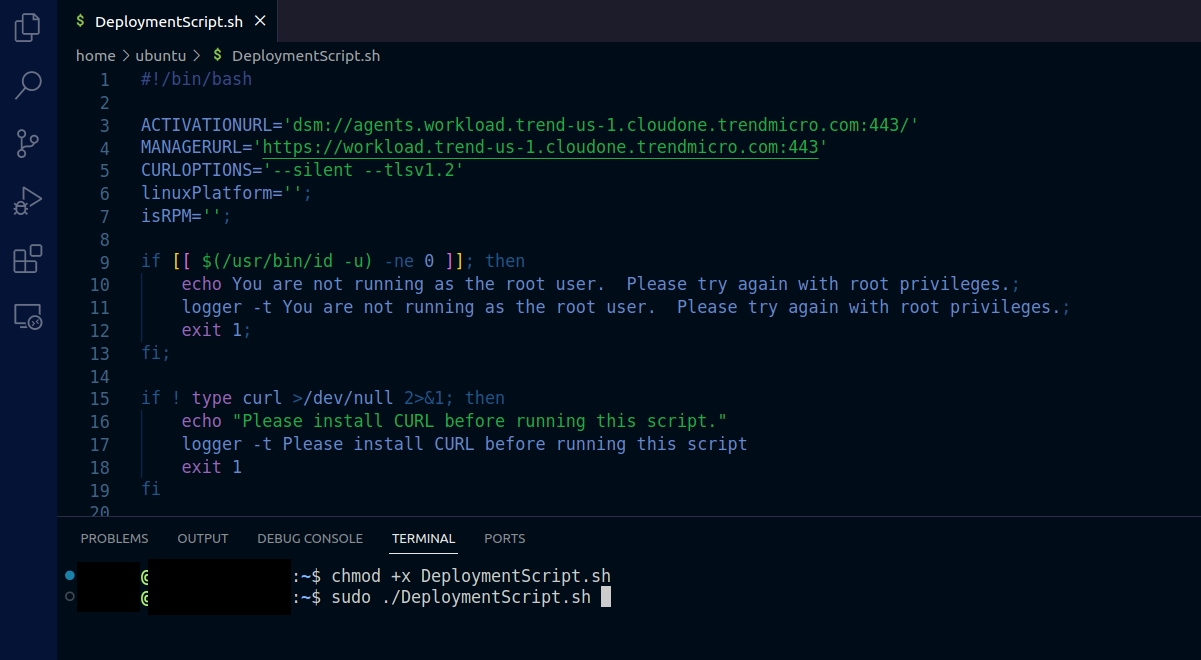
1.5. Give execution permission to the file
- Type the command
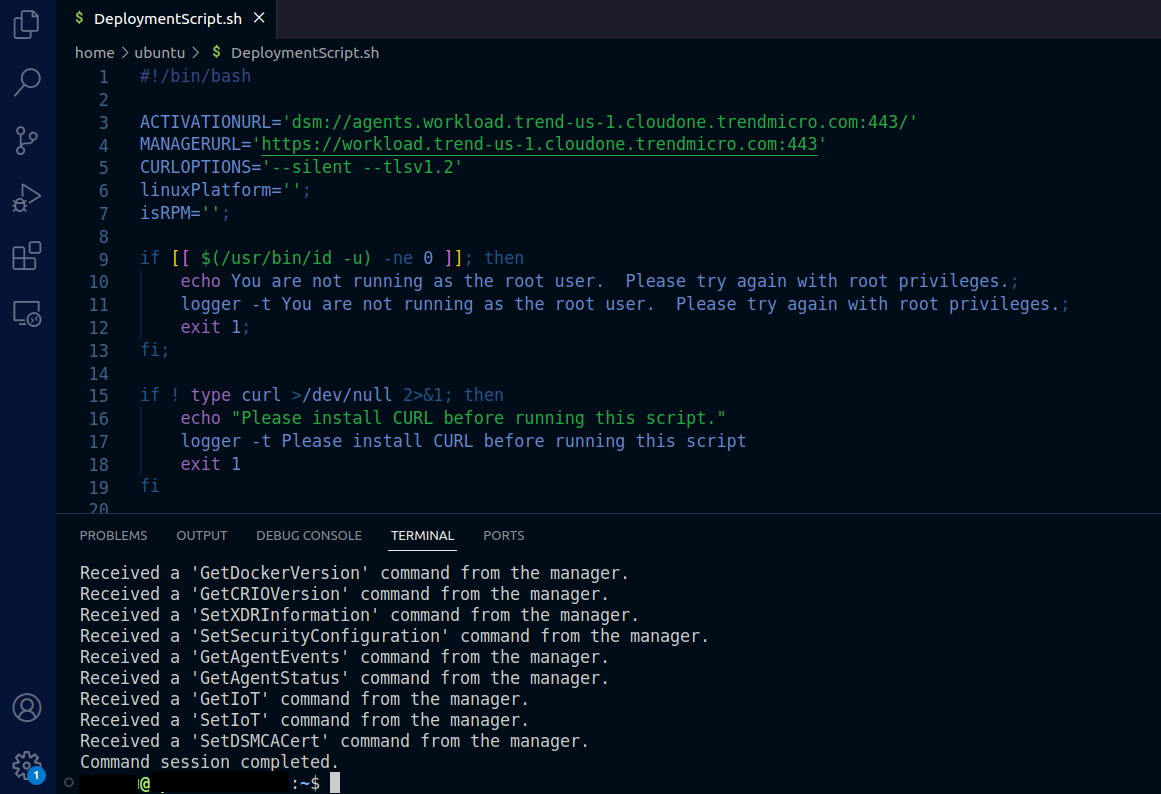
chmod +x DeploymentScript.sh - Execute the file
sudo ./DeploymentScript.sh
1.6. Wait until the agent is downloaded and instaled
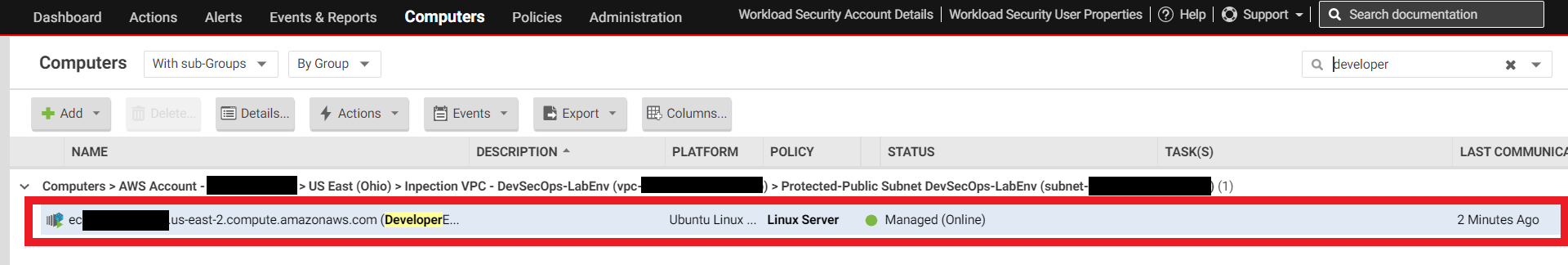
1.7. Go back to the console
- On the Computers tab
- Search for you Computer name